By Brayan Sanchez
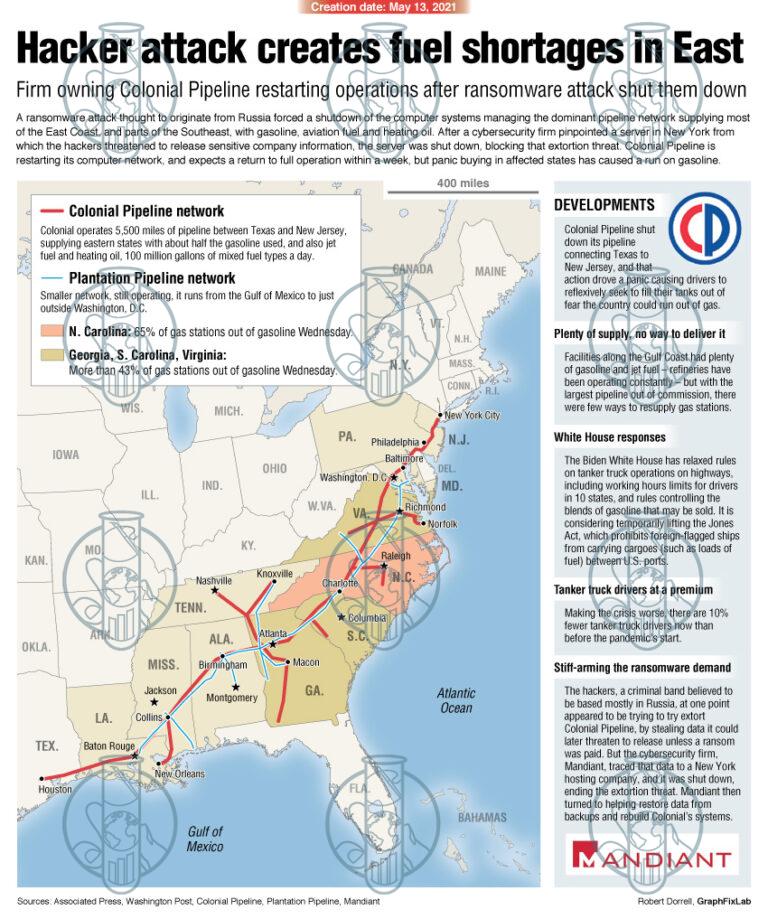
In May 2021, the DarkSide cybercriminal group launched a ransomware attack on Colonial Pipeline, which supplies 45% of the East Coast's fuel. Hackers gained access through a compromised VPN password lacking multi-factor authentication (MFA), encrypting IT systems and stealing 100 GB of data. Colonial Pipeline paid a $4.4 million ransom in Bitcoin, though the FBI later recovered $2.3 million.
The attack led to fuel shortages, panic buying, price spikes, and economic disruption. In response, Colonial Pipeline enhanced cybersecurity, while the U.S. government issued new cybersecurity regulations for critical infrastructure. The Biden administration introduced an executive order, and the TSA enforced new pipeline security mandates, emphasizing stronger cyber defenses to prevent future attacks. This incident highlighted the vulnerability of critical infrastructure to cyber threats.
The attack was carried out by DarkSide, a cybercriminal group believed to be based in Eastern Europe or Russia. DarkSide operated as a ransomware-as-a-service (RaaS) organization, meaning they provided hacking tools to affiliates in exchange for a share of the ransom payments.
DarkSide deployed ransomware to encrypt Colonial Pipeline’s IT systems, forcing the company to shut down its 5,500-mile pipeline that supplies nearly 45% of the East Coast's fuel.
Primarily for financial gain, as DarkSide was known for targeting companies with high ransom-paying potential.2. DarkSide claimed they were not politically motivated and only wanted money.